A lot of people out there know what Phishing is these days. Most know we need to be vigilant about watching what we click and put our information in out on the internet. But, it might be time to be even more so.
Personally, Attackers have attempted to hit me with at least two attempts in the last week alone! We have received numerous calls asking for advice and what to do to stop it from happening, several of our friends have been victims of credit and identity theft. But the sad reality is, there’s not a lot we can do other than educate ourselves on how it’s happening, how to recognize the threat, and what to do if it happens.
Social Hacking
So what is going on? Well, the basic attack style that is happening and running wild out there works like this.
The Phishing Cast

- At least one, but more than likely several of your friend’s accounts have either been compromised (hacked) or the attackers have taken the time to recreate your friends profile and make it look rather convincing, under a similar looking alias.
- They send you a convincing message or post that you will find nearly irresistible. Sometimes its something embarrassing, sometimes its something surprising. The last one I got was a simple post that showed it has over 6,000 views. Whatever it is they send you, it triggers the “Wow! I better click this and see for myself!” response in your brain.
- You click it and all of a sudden you have to login again.
- After you put your login information and you are prompted with just the main social media site you just logged into.
The Hook and Landing
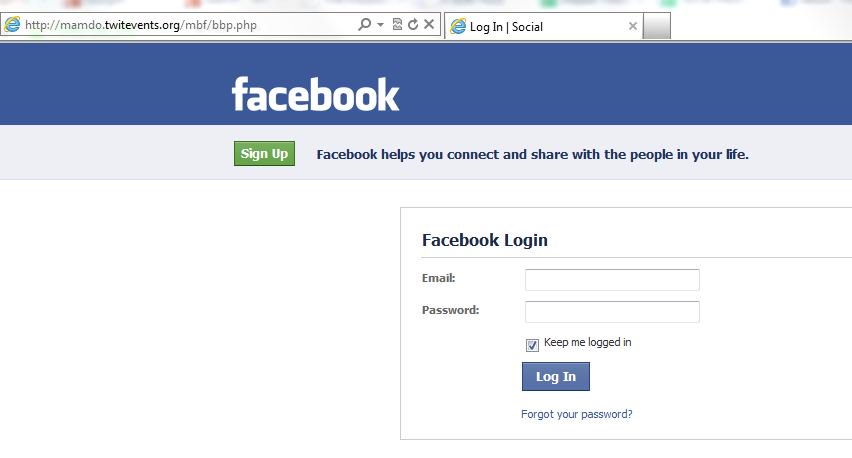
So what happened? Well, the bad guys just got your account information and are likely already sending the same phishing attempt to your friends they got from your account, except that now it’s coming from your account.
Remember Step 3? Yea that was a fake site that looked exactly like the real thing, and you just put your username and password in there. Which means they know it now.
It gets worse. A lot of us (including myself at one point in time) have used the same username and password for multiple accounts and services. That means they also have your login information for those as well. Your email, your other social accounts, your bank accounts. You should treat them all as compromised.
Recovering from being hooked.

So you fell for it. Time to crawl in a corner and hide. Right? No. But time is what determines how bad an attack will affect you.
Most of the sophisticated attacks we see today are automated. This means that the hacker would not be envolved very much with the process at all. He relies on scripts, worms, trojans, viruses and other malware to do the bulk of the work for them. What this means to you for that password you just typed in, is that the automation process is going to start looking around on the web at other services and attempt to login with those same credentials, and for every success, it logs and sends it to the hacker for use later.
Even though it is mostly an automated process it takes time for the attacker to use the information gathered. So we have a small window that can prevent a small issue from becoming a life-changing event. Here is the step by step of how we remediate these instances.
Remediation
- Don’t panic. Easier said than done when you know your financials and reputation are on the line.
- Cut the head off the snake, reset the password and enable 2FA, or disable the account, do something that will stop the known security breach from spreading more.
- Depending on the situation we sometimes recommend announcing to your followers, email contacts, etc that you had experienced a security breach and not to open any attachments that have been sent by you. It is generally better to show effort in protecting others than to be found later that you did nothing.
- Execute your remediation plan, if you have one. Ok I know, nearly no one has that. (But you should) So here are the basics, we believe and teach the same method as CISSP Risk Management, but you have to think in multiple dimensions. The typical instinct would be to protect your bank accounts and financial assets first. And that may be true in a lot of situations. But consider a large corporation or health care facility with millions of patient records, would their FDIC insured financial accounts be more of a Value/Threat based risk than the remediation costs for having those patient files leaked? Ultimately it comes down to is to prioritize what will hurt you or your business the most and act!
- Change all of your passwords on all of your accounts, not just the one you know were compromised and enable 2FA where you can. (Yes this is a lot of work)
- Flop back into the water, Take this as a learning experience, tell your friends to be cautious and not to bite everything that is shiny.
Phishing Prevention
As with most things. Prevention is better than attempting to cure. So how do you prevent being phished? The best way, like any smart fish or phish, is don’t fall for the bait.

- Be suspicious of unusual activity. Does the person contacting you usually contact you? Do they usually send attachments?
- The hover check. This use to be a great way to verify something is legit. But now we’ve seen some vulnerabilities with some platforms that are being used that can make a link look legitimate, but then it forwards to the phishing site. Basically, if you hover over something you think is ok, the domain in the URL matches up and you think. Oh ok, this is real. Then you click it you are redirected to the attack site you can see this from the URL at the top of your screen and it will not be the same thing you clicked.
- Treat every login screen as a suspect. Most services allow our phones and computers to cache our logins so we don’t have to login every single time. With the exception of banks and higher security services.
- ENABLE Two Factor Authentification!! (2FA) Yes, this needed to be exclaimed. It is one of the best protections we have available right now. Yes it is a pain to have to send a code to your phone to verify that it is you, yes you are correct its not a perfect solution, but every layer of security you have in place gives the bad guys one more layer to get through, and this one is pretty thick, unless they stoled your phone number, your phone, or whatever other methods of authentification you decided to use. The thing with 2FA is even if an attacker gets your username, password, date of birth, blood type, SSN, Pet’s name, Middle name of your second-grade teacher, etc, etc. They will be presented with the dreaded “Please enter the code we sent to your number ending”. And now they are stuck unless they call you and ask for the code and you give it to them (With-in 60 Seconds).
On behalf of all IT Security professionals, This is the closest thing to a “cure” we can provide. Treatment and prevention is currently the only solution.
Be vigilant, and we can stop all of this, it’s up to us.

